February 25, 2025
Phase 6: Lessons Learned
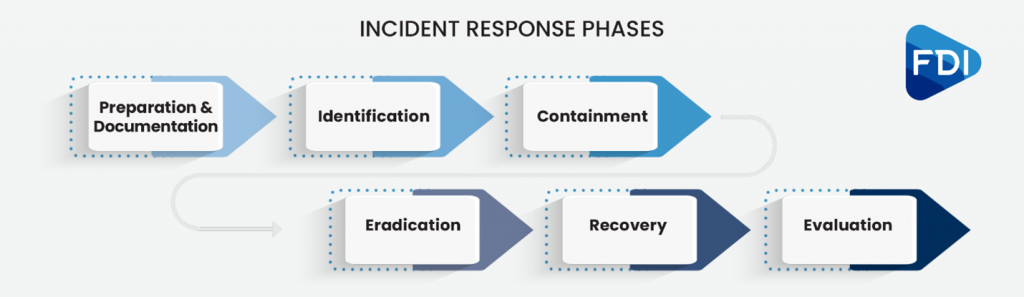
A successful Incident Response Plan (IRP) will be your guide through any type of disaster that impacts your business, from a ransomware attack that locks up your data to a hurricane that destroys a data center to a power outage that makes your systems unavailable. The plan will take you from those first stressful moments of discovering the threat to your business operations through identification and prioritization of the problem, containment, eradication and finally the recovery phase. (Be sure to read our blogs on Why You Need an IPR and Phases 1-5. Links below!)
Before taking the pats on the back for a job well done, it’s time to dig into the final phase of your IRP: a post-incident analysis of the lessons you’ve learned and how to incorporate that information back into your IRP.
IRP as a Living Document
According to the National Institutes of Standards and Technology (NIST) Computer Security Incident Handling Guide , taking the time to review the entire scope of the incident and how you reached a successful recovery is often overlooked or forgotten. It’s understandable. Work duties and processes don’t stop, and new problems are always coming up. In 2023, there were nearly 8 trillion intrusion attempts worldwide , and more than 5 billion cyberattacks. With a constant onslaught of potentially malicious cyber incidents, incident response teams need to constantly look forward and be ready for the next problem.
However, holding a lessons-learned meeting immediately after a major attack or in regularly scheduled sessions to discuss the smaller and ongoing incidents is important to keep the IRP up to date. Threats are constantly evolving and new tools and solutions are introduced into the network. Taking the time to understand what happened to cause the incident and how you reached recovery provides the background information that will improve overall security within the organization and offers suggestions on how to better address the next incident.
Questions to Ask About Your Incident Response
The success of the post-incident analysis depends on the agenda. NIST offers a list of questions that will get the conversation started and ensure that important topics aren’t forgotten:
- Exactly what happened, and at what times?
- How well did staff and management perform in dealing with the incident? Were the documented procedures followed? Were they adequate?
- What information was needed sooner?
- Were any steps or actions taken that might have inhibited the recovery?
- What would the staff and management do differently the next time a similar incident occurs?
- How could information sharing with other organizations have been improved?
- What corrective actions can prevent similar incidents in the future?
- What precursors or indicators should be watched for in the future to detect similar incidents?
- What additional tools or resources are needed to detect, analyze, and mitigate future incidents?
From the information gathered, the team should then create a report for each incident that can be used for reference during future, similar incidents. Detailed recording will also be valuable for evidence in legal proceedings or to prove compliance regulations have been met.
Using Feedback to Improve Overall Corporate Security
The results of the lessons learned in an incident aren’t meant to be hidden away until they are needed again. Instead, they can be used to improve the overall security posture in your company. Use the results of lessons learned to:
- Update your security awareness training.
- Train new members of the incident response team.
- Set rules around devices, new technologies and data access.
- Review security tools.
- Determine the need for an outside partnership with a managed service provider to improve overall security approach.
Nobody wants to be the victim of an incident that takes business operations offline or compromises data, but the reality is, at some point, every organization will face a serious incident, whether it is a cyber attack or a natural disaster. Preparing for that day with an IRP is key to ensuring your organization is ready to manage that event.
Download our IRP Planning Document : Create Your Incident Response Plan
Catch up on our IRP Blog Series
The post The Post-Analysis of the Cyber Incident: Why You Should Review the Lessons Learned appeared first on Fairdinkum.


