February 19, 2025
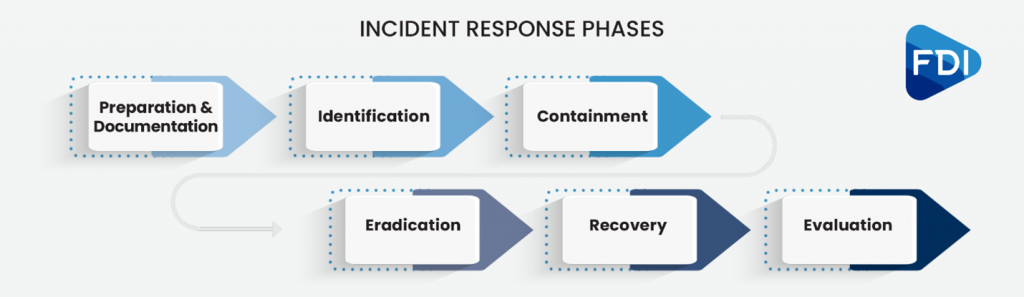
Phase 5: Recovery
In your Incident Response Plan (IRP), Phase 4 (eradication) goes hand-in-hand with Phase 5 (recovery). In fact, in the National Institutes of Standards and Technology (NIST) Computer Security Incident Handling Guide, eradication and recovery are grouped together in one section, stating “eradication and recovery should be done in a phased approach so that remediation steps are prioritized.”
Recovery is the third actionable step of incident management. After containment and eradication of the intrusion that caused the incident, recovery is the process to restore your systems to a clean configuration that is as close as possible to the pre-incident environment. In this phase, the incident response team will take steps to ensure the systems are working normally and that any lingering vulnerabilities are remediated. According to NIST, during the recovery phase you will take basic actions that include:
- Restoring systems from clean backups
- Rebuilding systems from scratch
- Replacing compromised files with clean versions
- Installing patches
- Changing passwords
- Tightening network perimeter security (e.g., firewall rulesets, boundary router access control lists).
Data Integrity Analysis
Getting your systems back to normal operational standards is the first step in recovery. The second is to verify data integrity. Data compromised during a cyber incident could be corrupted or modified. Even backup data could have been impacted by the incident, so that, too, must be analyzed.
Verifying data integrity involves running checks and audits to see if the data has been altered or tampered with at any time during the cyber incident’s activity. All data should be checked for anomalies, missing pieces, skewed information and unauthorized modifications. The data can be validated using audit trails, logs and older, clean backups to verify any changes or deletions.
If data is found to be compromised, the incident response team will need to isolate the impacted files and systems as quickly as possible. Legal and public relations members of the team will work in tandem to notify affected stakeholders and assess liability concerns, while other team members begin the remediation and recovery process.
The National Cybersecurity and Communications Integration Center (NCCIC) recommends the following action if data is compromised:
- Don’t turn off the system or disconnect from the network because this could result in a loss of forensics.
- Don’t install any new tools except to run programs necessary to image the system.
- Do memory captures and hard drive imaging because this can present important incident timeline information.
Ongoing Recovery to Stop Repeat Attacks
The recovery phase doesn’t end once the system appears to be back to normal and all data is recovered and secured. “Higher levels of system logging or network monitoring are often part of the recovery process,” said NIST. This is because once threat actors have figured out how to get into one part of the system, they will surely continue to try the same or similar tactics to get into other areas of the network.
Recovery is an ongoing process that will require a number of procedures and tools, including:
- Continuous monitoring of restored systems to confirm there are no lingering threats
- Vulnerability assessments to catch potentially exploitable holes in the system
- Regular penetration tests
- Tabletop exercises to make sure the security systems are working as designed
Once recovery is done, there is just one more phase to complete your IRP and help improve your IRP for future situations.
Phase 6—the post-incident evaluation to document the lessons learned.
The post Restoring Normalcy to Your Compromised Network appeared first on Fairdinkum.


